OpenSSL - Private and Public Key check
A very common need before deploying the certificate to the server is to compare the mutual match of the private key and the issued certificate. These are always a few keys that must belong together. Otherwise, the certificate would not be installed, or worse, a key error could cause the site to malfunction. The interconnection also applies between the private key and the certificate request (CSR).
OpenSSL
To work with certificates, you need to have the OpenSSL library installed. See the OpenSSL for Windows and Mac OSX page for instructions and download links.
Keys verification
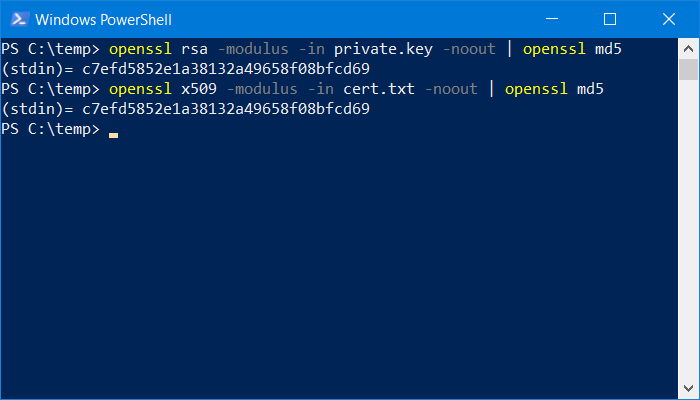
A sequence of two OpenSSL commands separated by a "|" character is used to compare keys resulting in a character string that must be the same for both keys. In this case, the tested keys belong together.
The following commands should be entered one after the other to generate separate outputs. The output is an md5 hash (fingerprint) of the key, it can be replaced by the sha256 algorithm, which, however, gives a longer string of characters. You can name the file extensions as you need and you are used to, for example .csr, .crt, .txt.
Comparison of the private key and the issued certificate:
openssl rsa -modulus -in private.key -noout | openssl md5
openssl x509 -modulus -in cert.txt -noout | openssl md5
Comparison of private key and certificate request:
openssl rsa -modulus -in private.key -noout | openssl md5
openssl req -modulus -in domena.csr -noout | openssl md5
Each command results in a character string. If the output of each command matches, the keys belong together. If the outputs do not match, the keys do not match and the certificate cannot be installed. The only solution is to generate new keys.
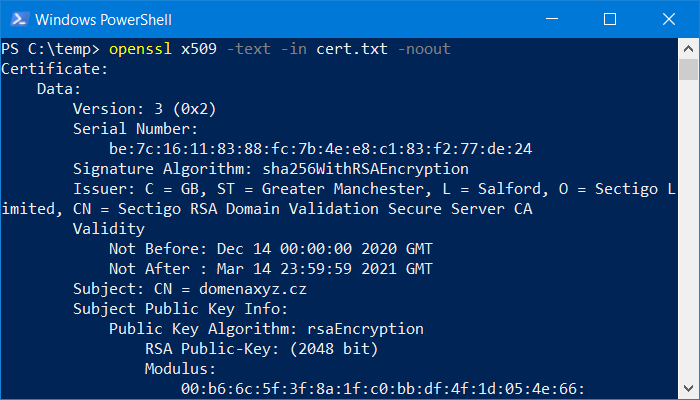
Display information of the issued certificate
Use the x509 command to check the issued certificate and its information. This can verify that the information in the certificate is correct and matches your private key.
openssl x509 -text -in cert.txt -noout
The output is a complete overview of the information of the issued certificate, including validity, expiration and data about the domain, or for corporate OV SSL certificates information about the company
Where next?
Back to Help
Found an error or don't understand something? Write us!






